Secure and Manage Web Access Across the Enterprise
Finally - an enterprise class browser built for centralized control and management
Request a Demo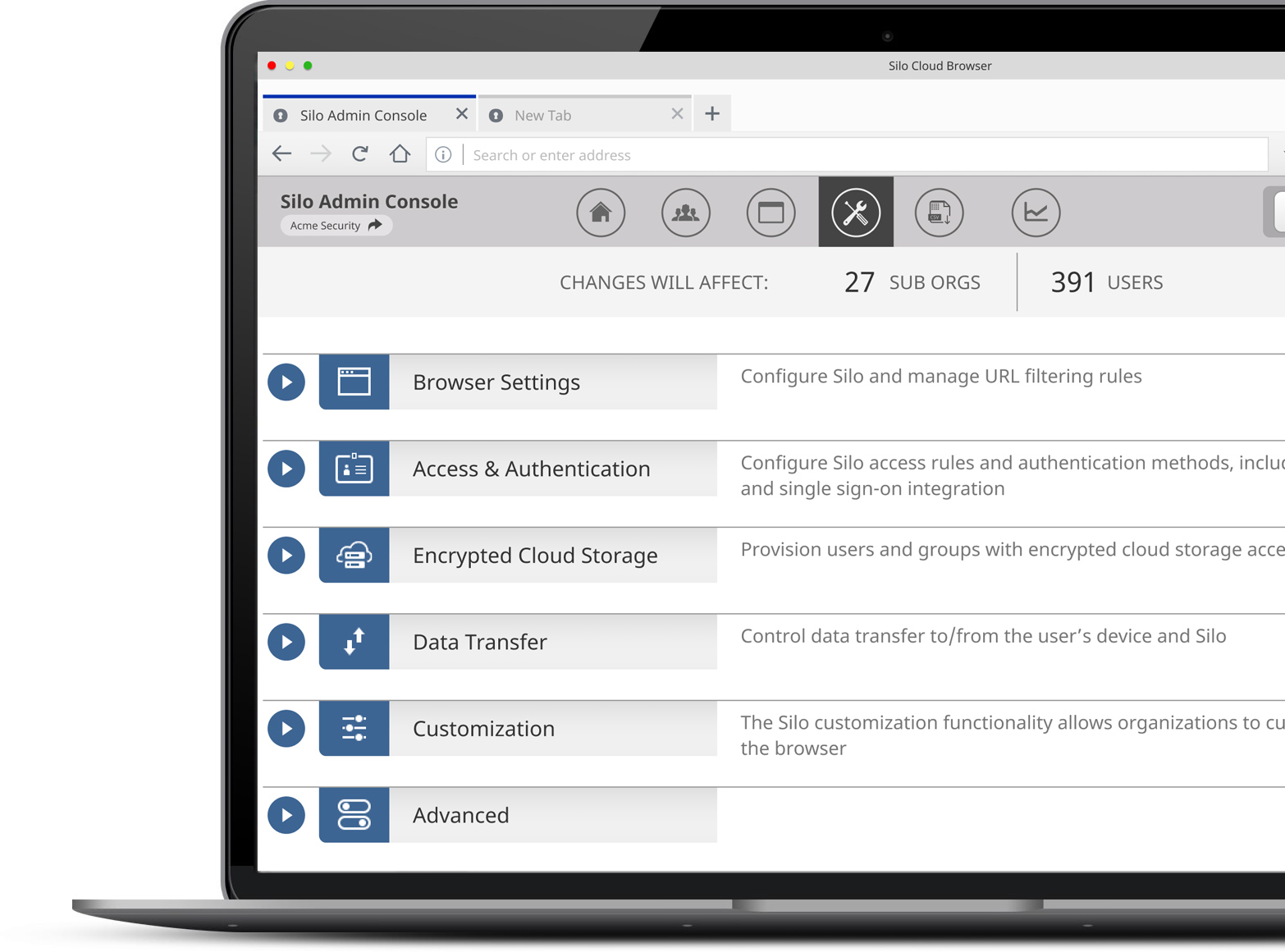
How Can IT Centrally Manage and Secure Web Apps and Services?
What used to be simple, when IT controlled devices and applications, and everything happened behind the perimeter, is now a free for all. There’s little distinction between work and personal computing. Users BYOD, networks are hot spots, and corporate data lives in cloud services.
IT pays the price to manage this risk:
-
Info-sec spending in 2018 was $114B, up 12%; hitting $170B in 2022 (Gartner)
-
Average enterprise has more than 70 security vendors (Cisco)
-
72% IT heads can’t find staff with appropriate cyber security skills (Dimensional Research)
20% of all SMBs say there is a high-to-definite likelihood their business would not survive at all after a successful cyberattack. - Cyberthreat Index for Business

Shift risk off-network while reducing IT complexity
Gartner says that 98% of external attacks occur over the web. That administrative pain IT feels is trying to secure and control the browser. Instead of managing a cocktail of multi-vendor solutions, shift the browser to the cloud. In a single stroke, organizations eliminate the biggest risk surface area, and improve IT efficiency.
Simplify your tech stack at the:
ENDPOINT • Reduce reliance on so-called Next Gen client side AV solutions
NETWORK • Eliminate TLS break-inspect infrastructure and CASB solutions. Reduce SIEM alert and analysis costs by eliminating web events
GATEWAY • Simplify SWG and URL categorization. Whitelist internal apps and redirect all other URLs
IN THE CLOUD • Eliminate CASB or other aggregation solutions to remediate cloud-related policy violations
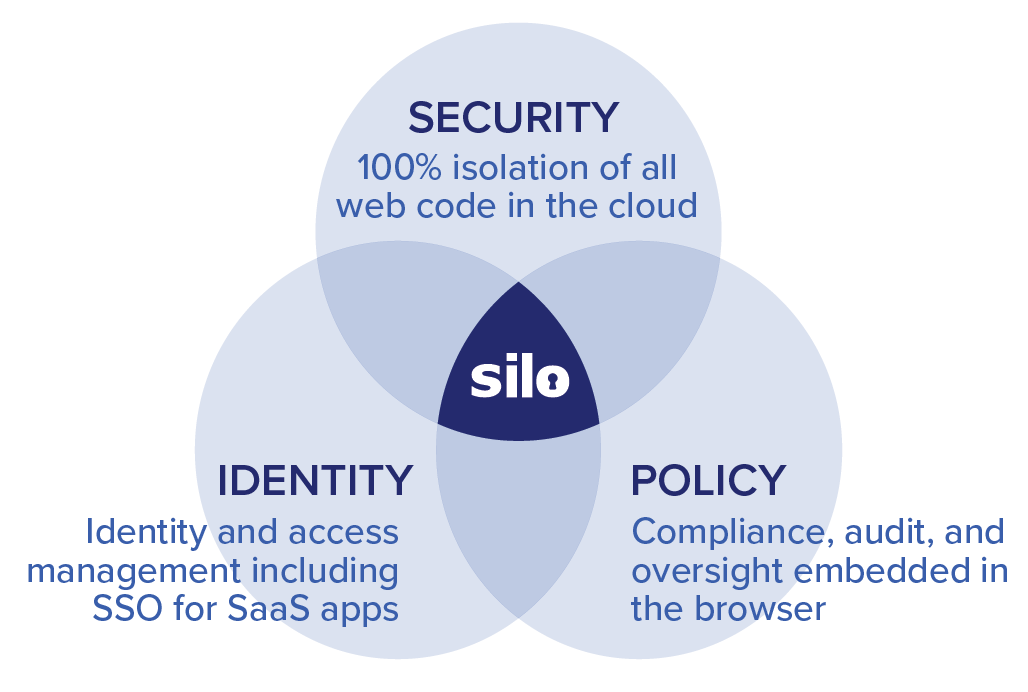
Silo lives at the intersection of security, identity and policy. Silo enables "follow me" control over security and compliance regardless of computer, network or location.
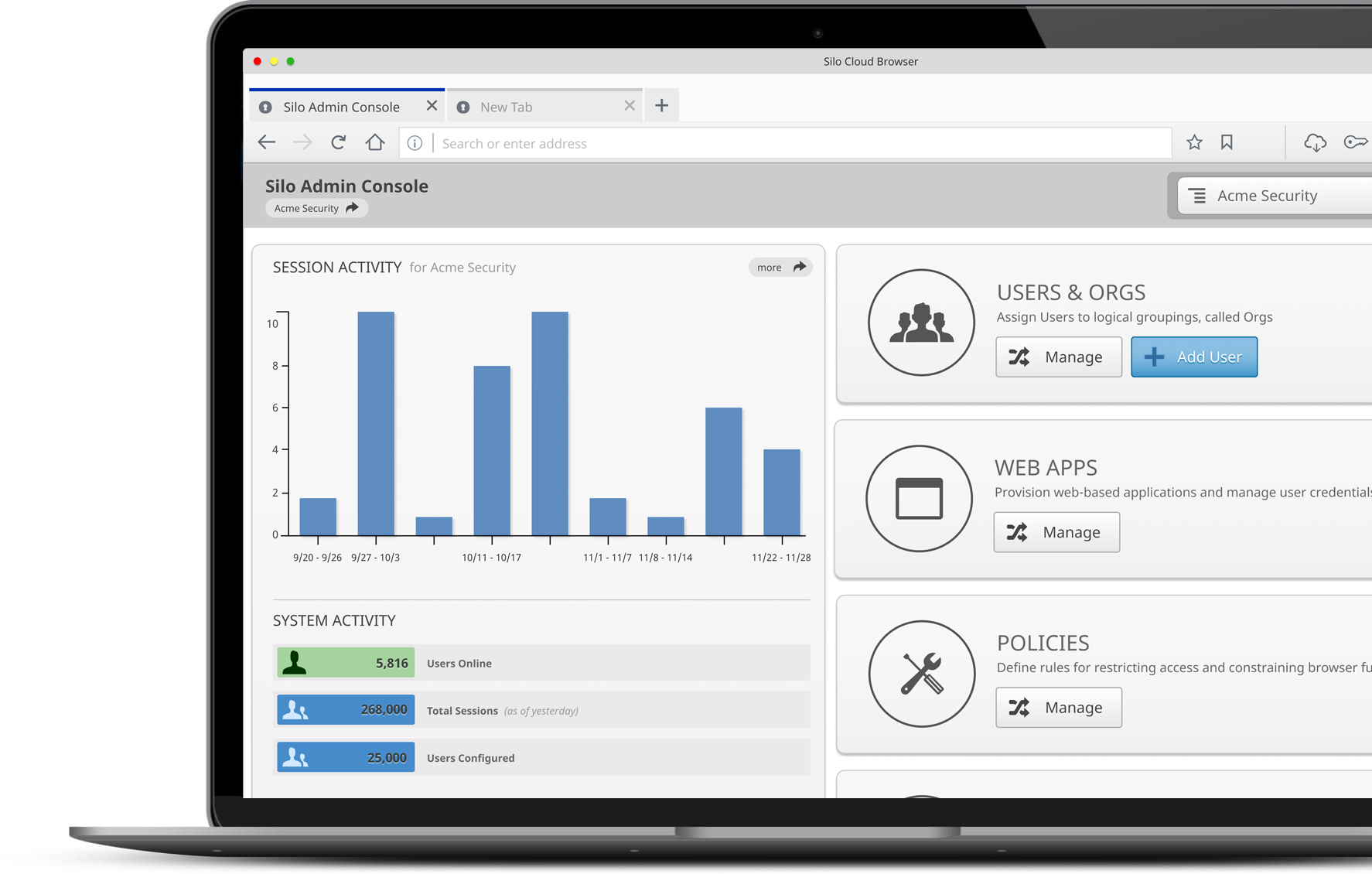
Proven efficiency gains
Based on our impact assessment survey, Silo customers have measured
-
53% Less time spent responding to security incidents
-
34% Less time spent managing exception requests
-
46% Less time spent on log analysis and reporting
-
30% reduction in bandwidth consumption
Enforce web policy no matter where users are

Silo enables unfettered access to the web
Enterprise IT maintains tight control on where users can go on the internet to prevent risk associated with uncontrolled, malicious or inappropriate content. Silo blocks all web code, including active malware such as trojans, trackers, and spyware. By executing all content in the cloud, users surf the web without risk or limitations.
-
Isolate endpoints from 100% of all web content - not just malware
-
Protect end-users from malicious email phishing links and downloads
-
Preserve anonymity and reduce targeting while users are online
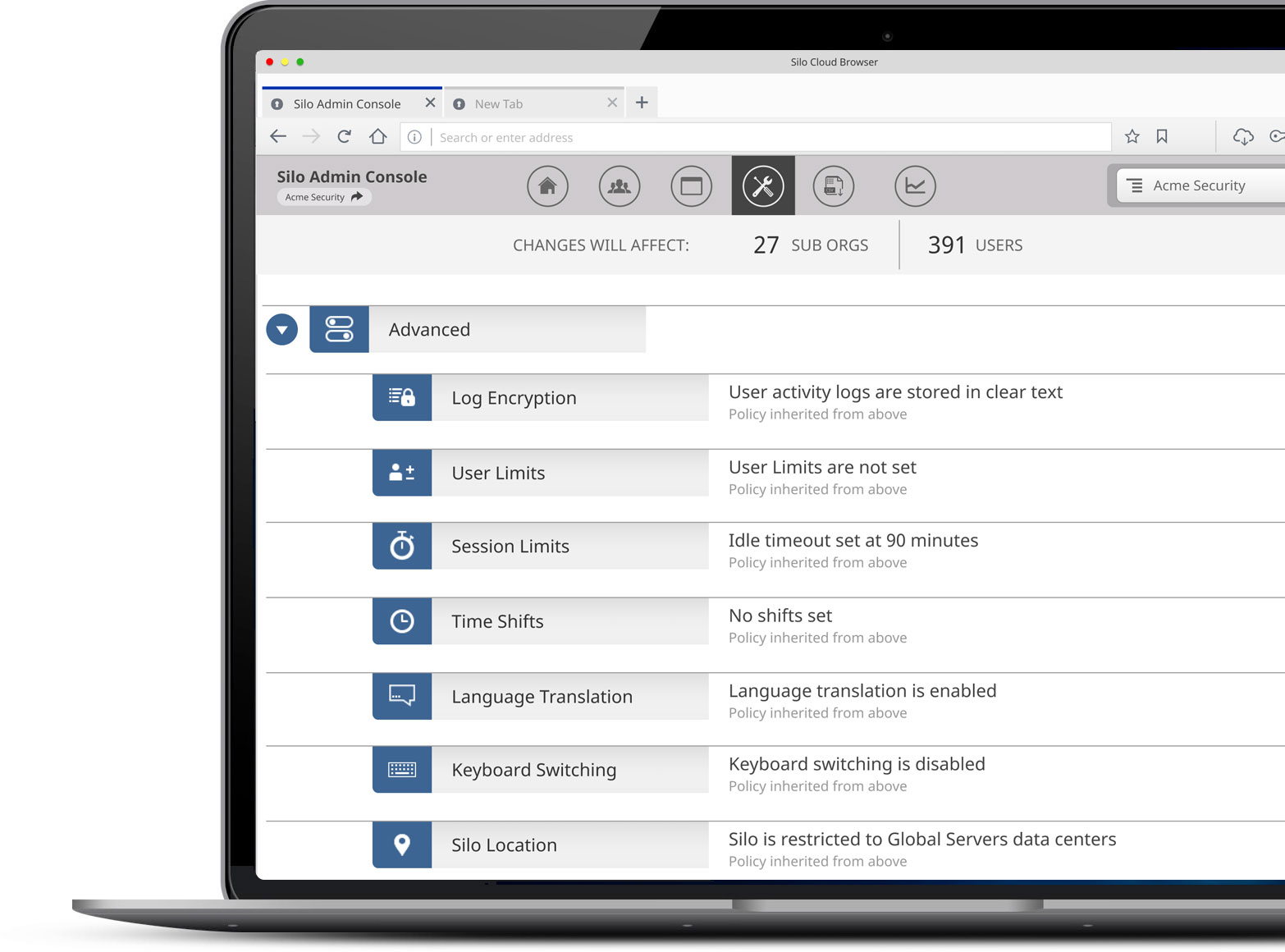
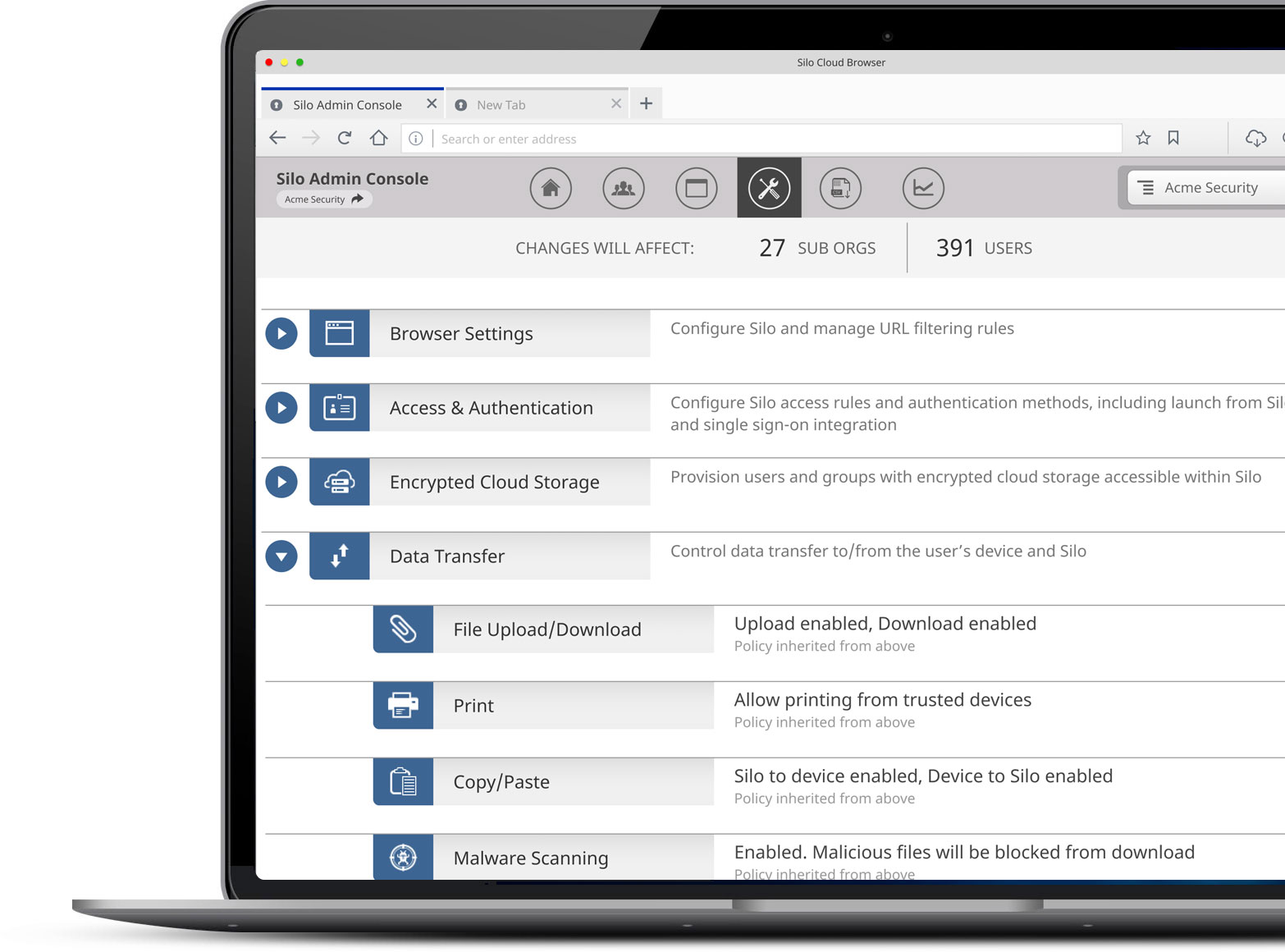
Access policy enforcement and authentication
Silo embeds policy, security and identity into the browser, allowing administrators to control the user experience with preconfigured user entitlements to websites, applications, and other web-based resources.
-
Access resources from both trusted and untrusted devices
-
Secure access to business-critical web-applications
-
Granular policies define data access based on predefined user entitlements to web and application resources

Integrates with existing identity solutions
User credentials can be managed manually - or automatically - with integration into Single Sign On (SSO) solutions. Silo integrates with AD and other Directory Services to import users and groups, speeding deployment.
-
Policy framework allows admins to quickly provision or revoke access
-
Granular policy allows customized user access and control
-
Works with Active Directory, Okta, Ping Identity, and more
Enterprise administration, security and control
By enforcing policy in the browser itself, organizations can define security, access and compliance requirements regardless of the user location, network or device. And with centralized, cloud-based admin controls, exceptions and revocation can be enforced without physical access.
-
Policies defined globally or by group, mirroring AD structure
-
Integrated data policies to enable or prevent upload, download, copy, paste, or printing of web-based data
-
Single kill switch to restrict access or remediate after policy violations

Logging for audit and reporting
Browsers have no centralized logging. Organizations need to collect endpoint, network or even cloud-based data via APIs to paint a full picture of end-user activity. Silo collects comprehensive user logs of all web-based activity, and allows organizations to encrypt their data with a key that they manage. Silo ensures visibility, non-repudiation, and compliance with Data Privacy Regulations for collection and review of audit log data - even for user activity over TLS/SSL links.
-
Centralized collection at the root or sub-group nodes for flexible oversight
-
Encrypted with a customer-managed key to prevent tampering or compliance violations
-
Authenticated API access and extract for integration with local analytics


