
More web exposure = increased risk
Access to the web is a practical requirement for businesses. Whether using cloud apps for job tasks, conducting research, or for personal reasons, employees spend ever more time in the browser. But given the design of the web, every page view means third party code crossing the corporate network and executing on the endpoint. Security solutions can’t keep up against rapidly evolving malware threats. Ransomware, phishing and other exploits are more targeted and coordinated. By allowing users to access the web from their local browser, organizations risk reputation, customer confidence, and the bottom line.
Gartner states that with 98% of external attacks coming from the public internet, organizations need an alternate approach to enable connectivity without increasing risk.
Detections of ransomware against business targets increased 195% in Q1 2019 alone, compared to Q4 2018. -- Malwarebytes

Empower your team with unfettered access to a risk-free web
Enterprise IT maintains tight control on where users can go on the internet to prevent risk associated with uncontrolled and malicious content. Silo blocks active malware such as trojans, trackers, and spyware by executing all content in the cloud, allowing users to surf the web without risk or limitations.
-
Isolate endpoints from 100% of all web content - not just malware
-
Protect end-users from malicious email phishing links and downloads
-
Preserve anonymity and reduce targeting while users are online

Containing risk in the cloud
Organizations today need secure and manageable access to business-critical applications and workflows. Authentic8's Silo uses browser isolation technology to ensure online access to corporate applications - without risking the enterprise.
Request a demoSilo for Safe Access stops ALL web-borne code from ever reaching the endpoint.

Eliminate downtime from ransomware attacks
Antivirus solutions have proven unreliable at catching ransomware and those failures can be disastrous for a business. With Silo, web-borne malware infections like ransomware never enter your network and never have access to local systems or resources. Silo keeps user productivity high and IT remediation and device re-imaging task to a minimum.
-
Reduce dependency on inconsistent, reactive security controls
-
Decrease support costs associated to web-borne malware infections
-
Enhance the overall security posture of the network
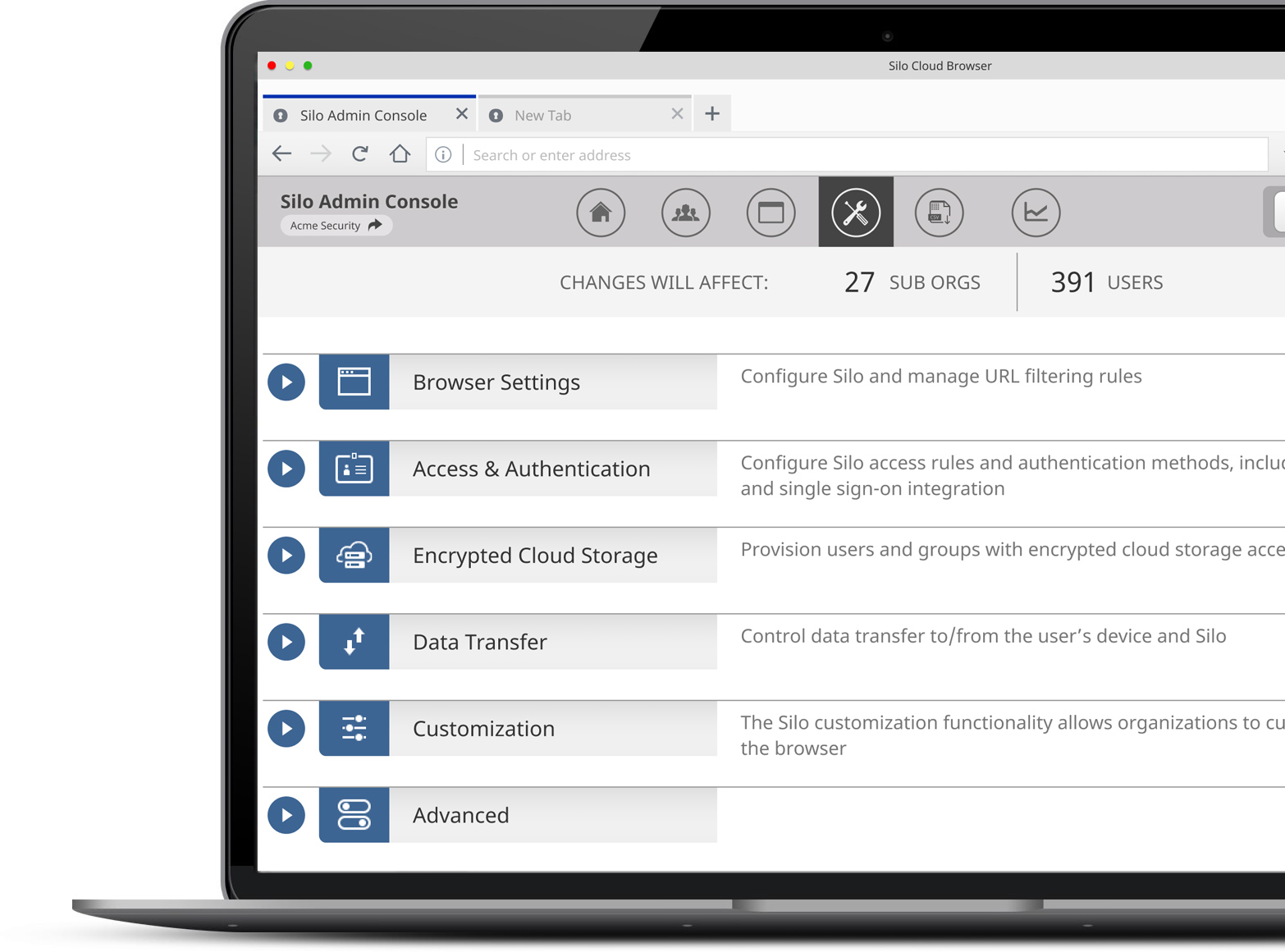
Embed web use policies directly into the browser
Proactively restrict user internet access with URL categorization and blocking of inappropriate or risky web content. Reduce page clutter and malvertizing attacks with user controlled or admin defined ad-blocking by domain.
-
Control Internet access for different users and groups
-
Block domains based on URL or content category
-
Custom content filtering by category or keyword
Enterprise administration, security, and control
By enforcing cybersecurity policy in the browser itself, organizations can define the user experience, security, access and compliance requirements regardless of the user location, network or device. And with centralized, cloud-based admin controls, exceptions and revocation can be enforced without physical access.
-
Policies defined globally or by group, mirroring AD structure
-
Integrated data policies to enable or prevent upload, download, copy, paste, or printing of web-based data
-
Single kill switch to restrict access or remediate after policy violations

Keep tabs on all web-based activity
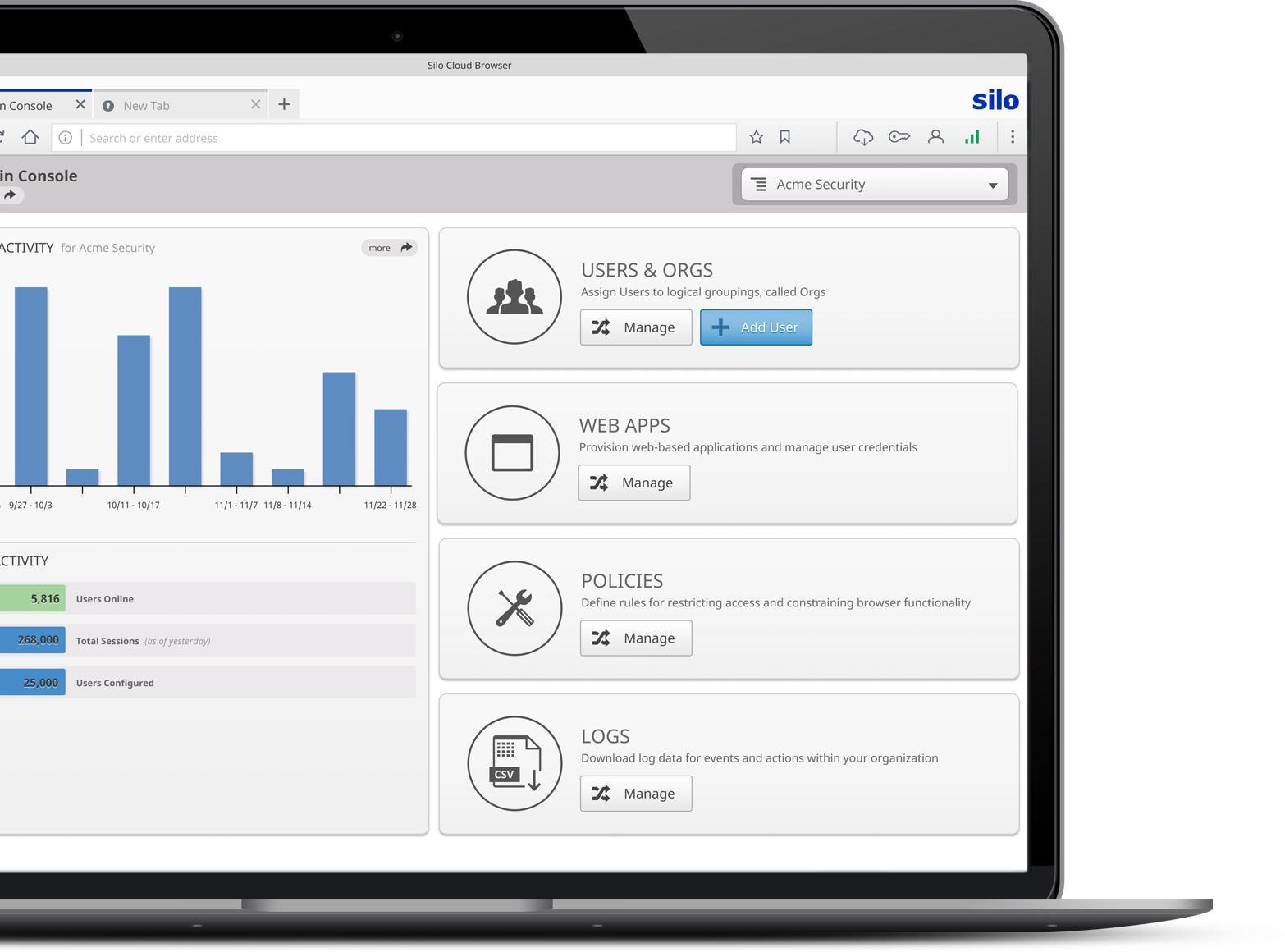
Browsers have no centralized logging. Organizations need to collect endpoint, network or even cloud-based data via APIs to paint a full picture of end-user activity. Silo collects comprehensive user logs of all web-based activity, and allows organizations to encrypt their data with a key that they manage. Silo ensures visibility, non-repudiation, and compliance with Data Privacy Regulations for collection and review of audit log data - even for user activity over TLS/SSL links.
-
Centralized collection at the root or sub-group nodes for flexible oversight
-
Encrypted with a customer-managed key to prevent tampering or compliance violations
-
Authenticated API access and extract for integration with local analytics


