Online Financial Fraud Investigations
Keep your online fraud investigations anonymous and secure while traversing the open, deep, and dark web.
Request a Demo
Escalating costs of financial fraud
For every $1 lost to fraud, the indirect spending associated with that loss is nearly $3. To regain control of these expenditures, financial institutions are fighting back to make online research and financial fraud investigations more cost efficient.
Using dedicated internal teams, banks, insurance providers, and financial services firms proactively scour the web to quickly expose and eradicate sources of fraud. Their ongoing efforts accelerate the investigative process, reduce external costs, and mitigate further financial risk.
-
Securely and anonymously gather online intelligence from open, deep, or dark web sources
-
Quickly implement and easily manage multi-user deployments - without the need for complex, dedicated infrastructure
-
Reduce costs associated with skilled IT resources, IT security management, and machine remediation and re-imaging due to malware related incidents

Reduce pressure on IT and investigation teams
The costs of setting up a dedicated research infrastructure are significant and require highly skilled IT resources to ensure secure and anonymous online investigations. Simple configuration mistakes can burn digital identities, while online activity and poor data hygiene can expose the investigation platform to malware, bad actors, and other malicious threats.
To streamline these costs, financial institutions deploying Silo for Research have saved an average of 89% annually over organizations that choose to deploy, maintain, and operate their own comparable, custom-built investigation platforms internally.
-
Protect research systems against all malicious web-borne code execution and malware propagation using cloud-based isolation
-
Mask online activity with user agent spoofing, browser fingerprint spoofing, and egress location spoofing
-
Reduce time, costs and resources needed to conduct successful investigations
In 2018, the Federal Trade Commission processed 1.4 million fraud reports totaling $1.48 billion in losses
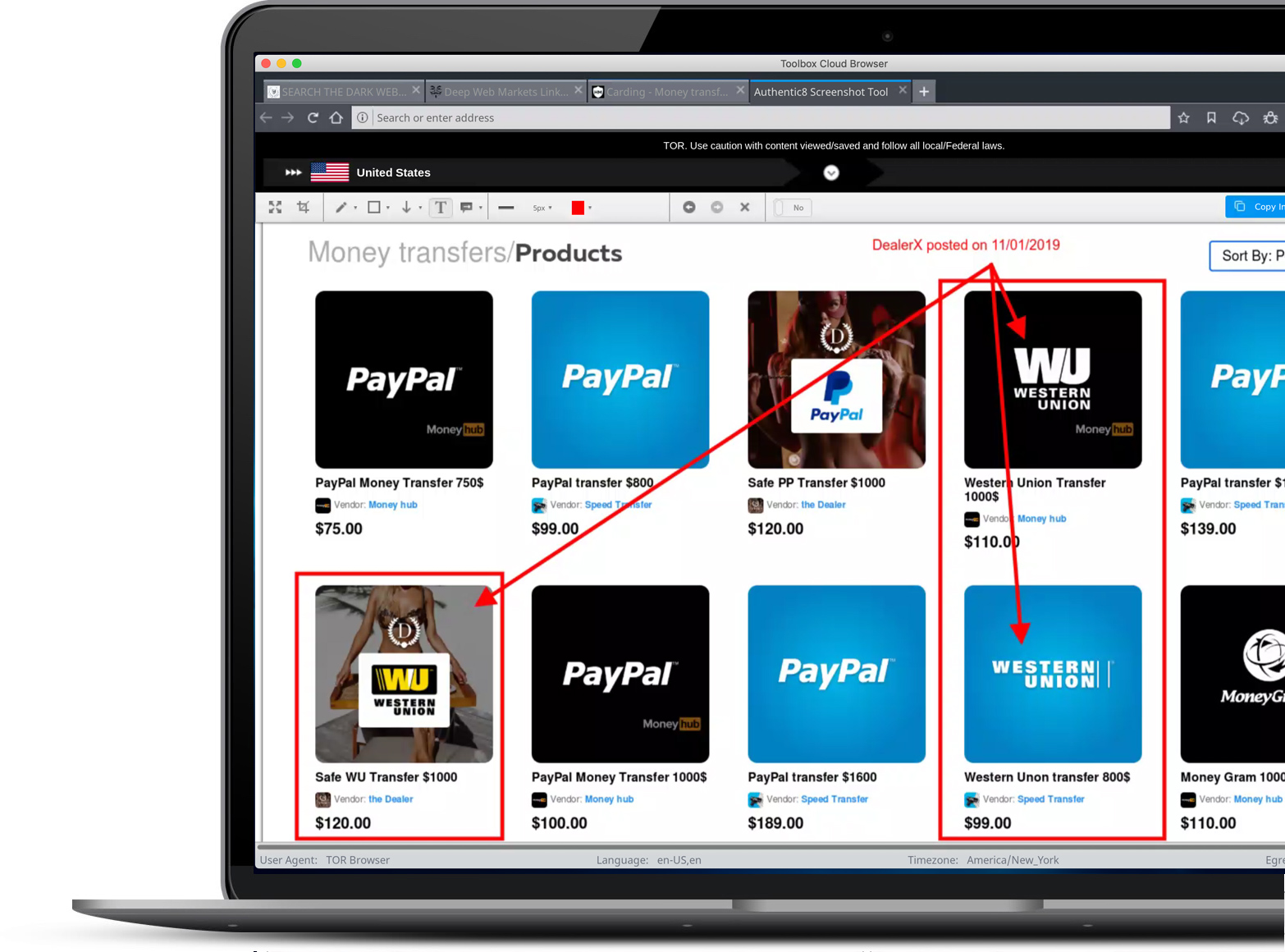
Collect evidence across multiple target properties and browsing sessions
Multiple, separate virtual windows support simultaneous collection actions across resources and networks. Share research materials with other investigators via secure cloud-based storage.
-
Page content flattening and capture with annotation and integrated, encrypted cloud-based storage
-
Out-of-band language translation to convert to the local language without disclosing analyst intent
-
Analysis of web source content and IP packet transactions for deeper investigation into counter-party resource

Cloud-based platform designed for secure, anonymous, and policy compliant investigations
Analysts are protected through virtualization, anonymous through attribution management, and compliant based on comprehensive audit and oversight. Encrypted cloud-based storage, activity time stamping, content hashing and encrypted audit logs ensure that evidence collection and production processes can be defended during proceedings.
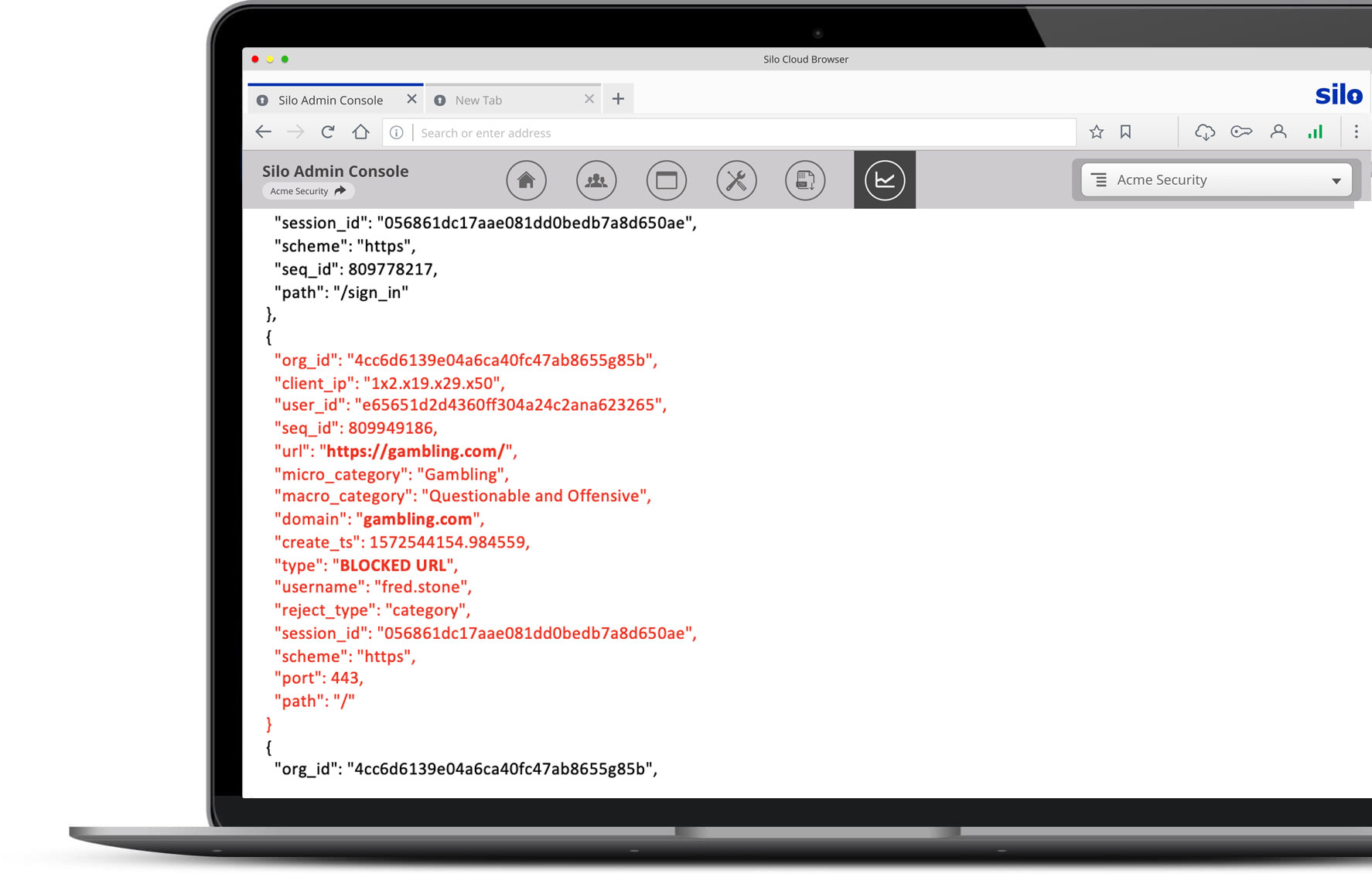
Enforce analyst usage and compliance requirements while conducting research
Analysts need to access web resources that fall outside of standard corporate policies. Silo for Research logs all analyst activity in encrypted audit logs. Compliance teams can review analyst activity and remediate issues. Customer-managed encryption keys maintain a proper chain of control for non-repudiation of activity logs
-
Centralized, comprehensive real-time logs of all user and admin web activity
-
Log data encrypted with customer-managed keys, with authenticated API-based extract
-
Download content timestamp and hash values logged to defend the authenticity of collections
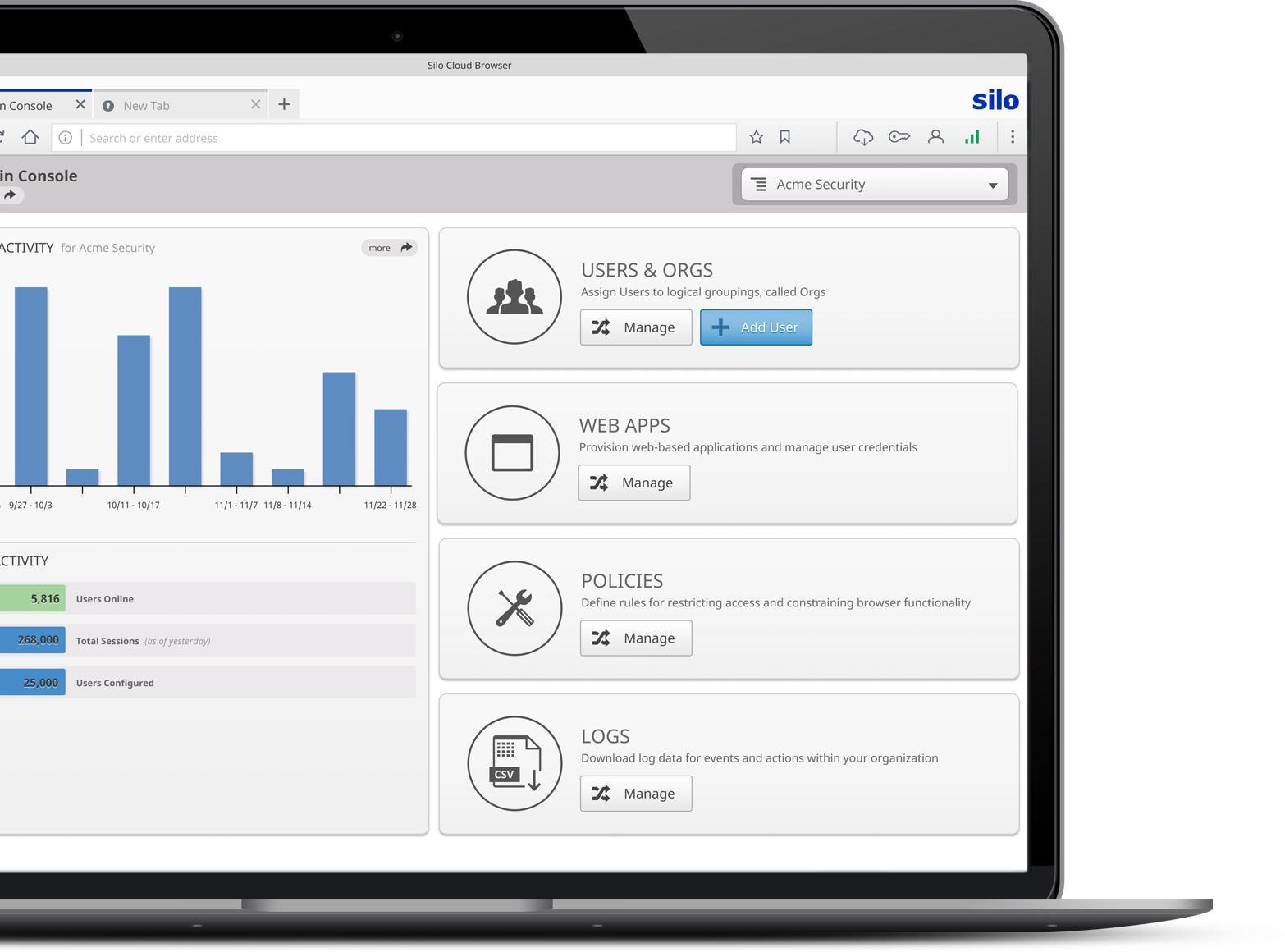
Enterprise administration, security and control
As a cloud-delivered platform, Silo for Research is administered and monitored centrally. Policies, entitlements, and audit can be managed globally or by sub-groups. Admins can sync Silo policies with Active Directory to mirror the organization's AD OU structure. And URL access, tool capability, and data policies can be defined based on specific workgroup requirements.
-
Centralized, cloud-based management of all user permissions and entitlements
-
A single platform for managing exceptions or revoking access
-
Enable device access rules to allow fully compliant capture from alternate devices or networks


