Silo for Safe Access (Cloud Browser)
Traditional browsers weren’t built with the enterprise in mind. Silo for Safe Access was.
Silo for Safe Access is a remote browser that embeds security, identity and data policies directly into the browser. Also with Silo available from anywhere and any device, policies follow users regardless of environment. By shifting exposure away from your network and devices, not only do you reduce your risk, but your internal process improves. With a configurable, centrally managed browser you unlock the power of SaaS.
How it works.
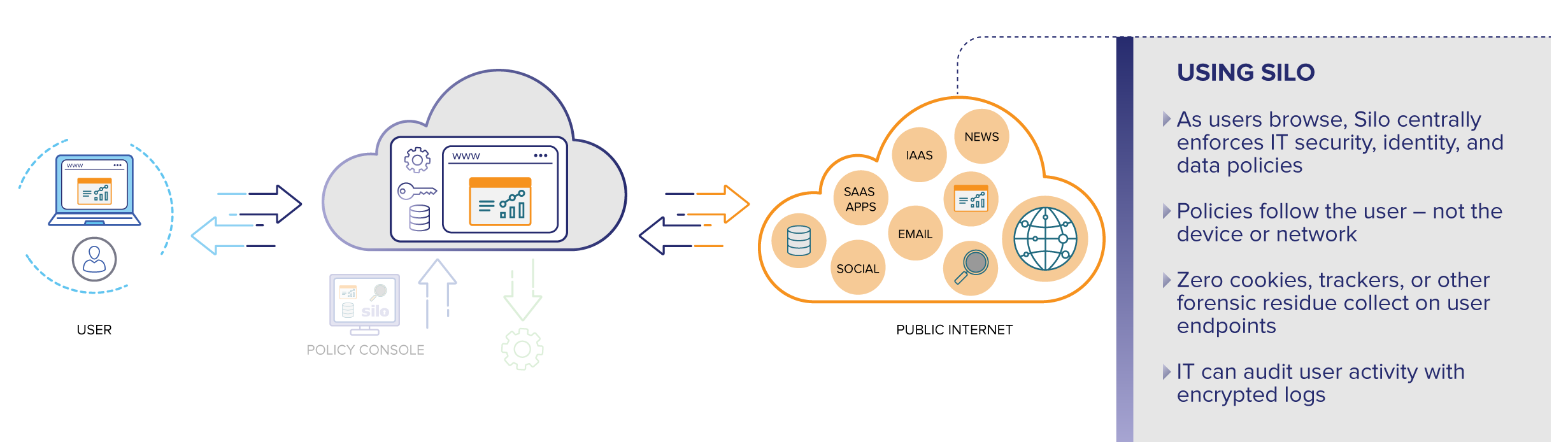
Silo for Safe Access embeds security, identity, and data policies into the browser.
The browser wasn’t built with the enterprise in mind. Silo was.
Centrally managed
Users aren’t behind your perimeter anymore and they don’t connect with IT-managed devices. Silo lives in the cloud where IT can enforce security and data policies regardless of user location or environment.
Policy enabled
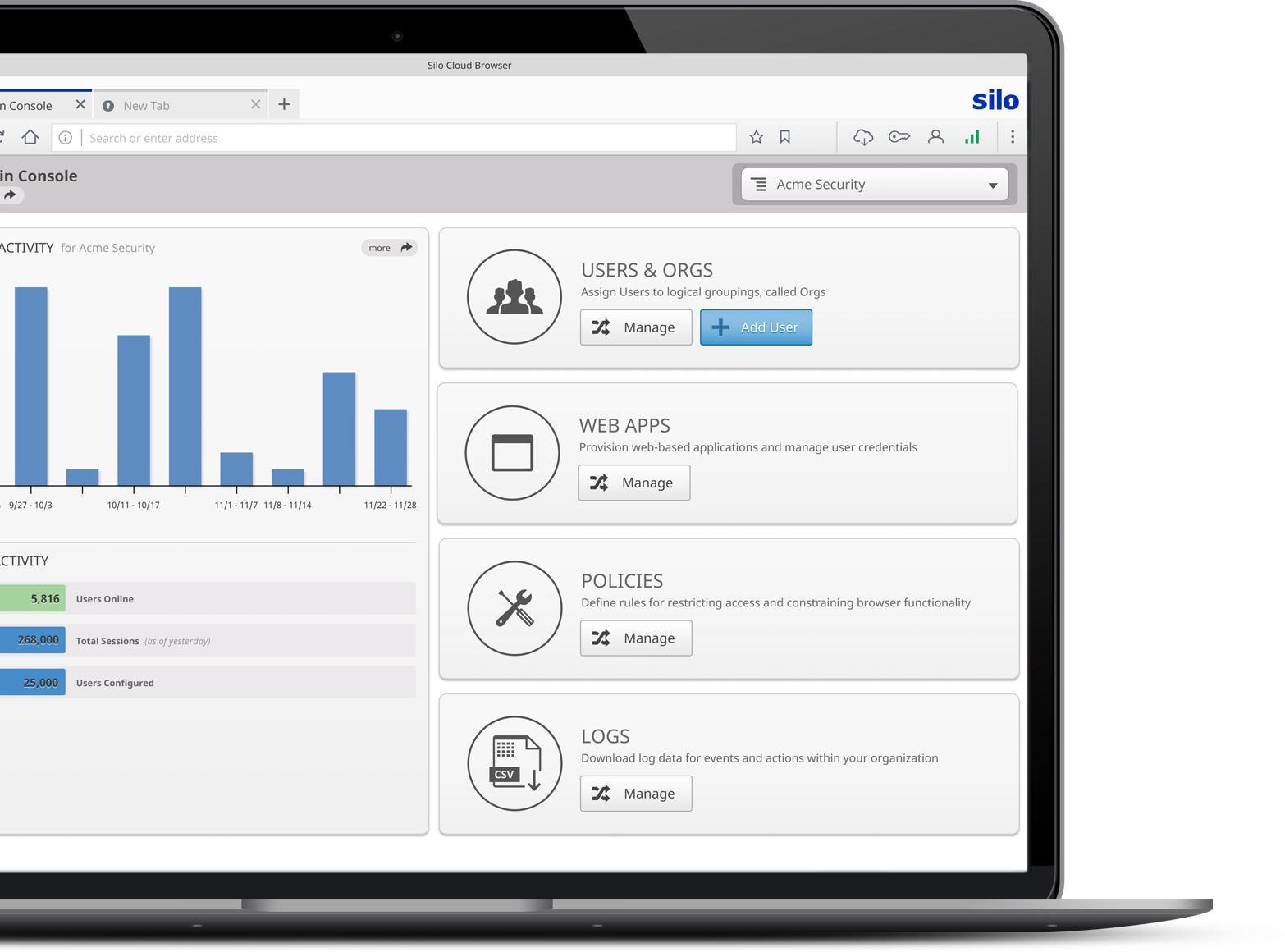
Silo's patented policy framework governs devices, data and websites across users and groups. Rather than the one size fits all tyranny of the traditional browser, Silo is configurable. And rather than static, rigid rules, Silo policies follow users, enabling access without increasing risk.
Fully auditable
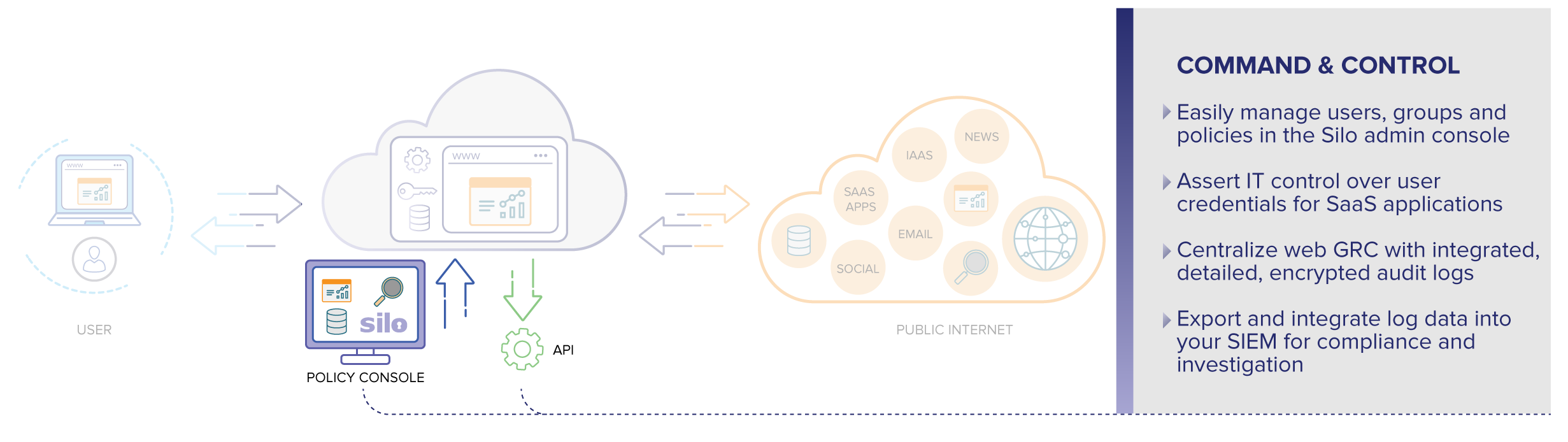
Silo gives you comprehensive, non-repudiable audit logs of all user activity in one place, encrypted with keys you control. No more collecting data across various security products or 3rd party websites. Silo instruments the browser for compliance and governance.
Silo customers can measure their bottom line impact. Once Silo for Safe Access is deployed, customers experience:
53%
Less time spent responding to security incidents.
46%
Less time spent on log analysis and reporting.
34%
Less time spent managing exception requests.
30%
Or greater reduction in bandwidth consumption.
Configurability is what makes Silo for Safe Access so revolutionary.
Strong authentication
Silo allows validation of users and devices, including multi-factor authentication.
Accessing web content
Users can type URLs directly, click links in other applications and render them in Silo, or configure the gateway to redirect URLs to Silo.
Device access policies
Users may have multiple devices or may need to work from devices outside of IT control. Silo policies can reflect device ‘trust’ as determined by IT so authorized devices get one set of entitlements, while others do not.
User experience
Silo sessions are accessed as a seamless, clientless experience via the local browser, or through a native, installed application.
IAM for SaaS apps
Silo includes a password manager that lets IT manage credentials to web apps. When combined with Silo policies, IT gets total control over access and use of SaaS apps, and a single switch to revoke access. And users never enter credentials into phishing sites.
Web category policies
Good governance follows users. URL category policies and white/black lists can be applied at the group or global levels. IT can enforce employee policies on content without worrying about the risk of grey-zone websites.
Directory sync
Silo policies are built on a hierarchical inheritance model, and can sync with your AD or LDAP instance. Adds, deletes and moves are mirrored between your infrastructure and Silo.
Gateway integration
IT can forward some or all URLs to Silo for secure rendering. Silo integrates with popular SWG platforms and can seamlessly redirect or redirect with a compliance page, depending on platform.
SAML federation
When you store information in Silo, proper authentication is required. Users can manage their own access, or IT can federate with SAML-compliant IAM platforms for seamless authentication and access.
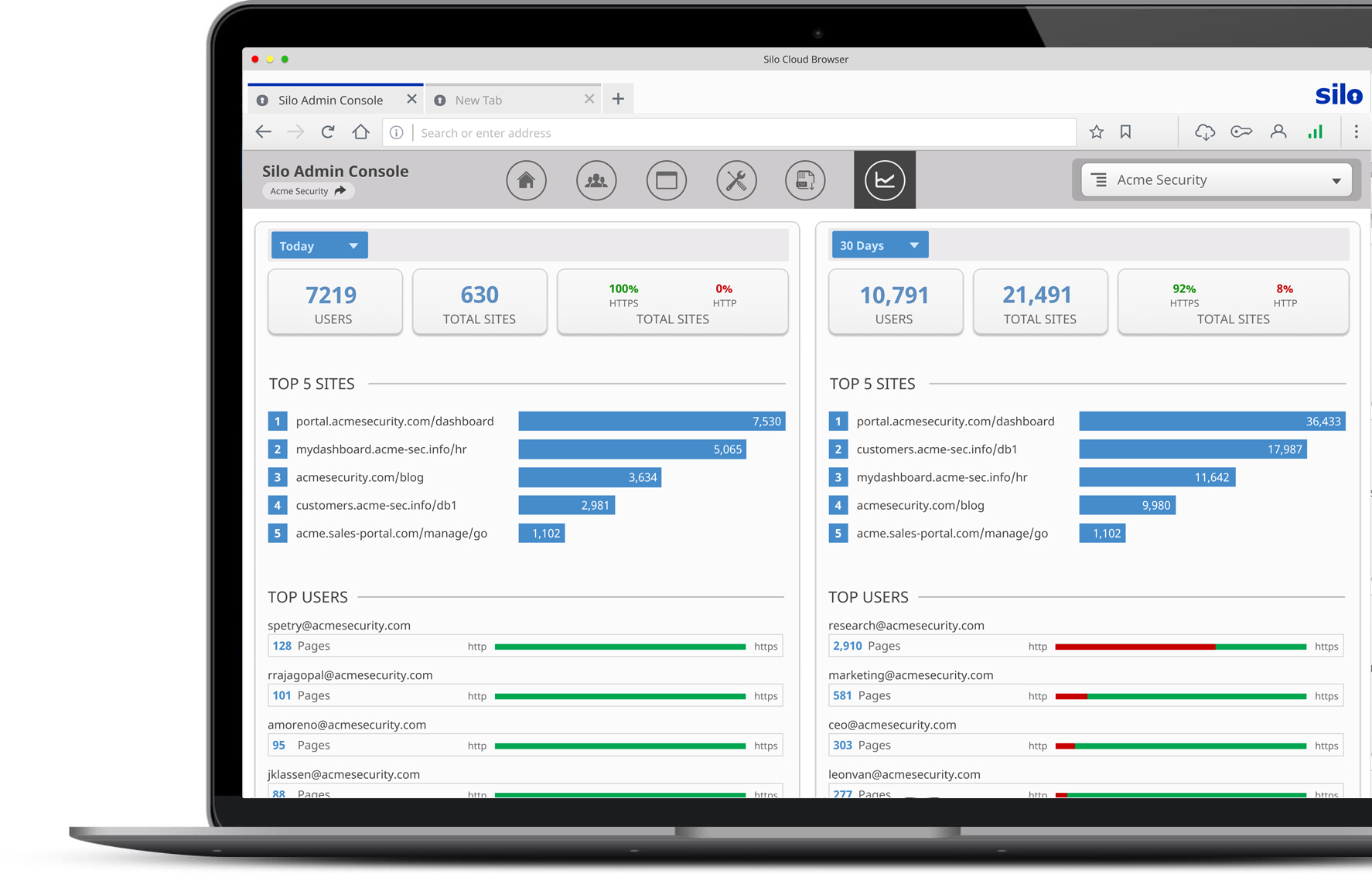
Silo flips the browser from a liability to an asset
Do the math. You’re spending more than you think trying to manage the web: On AV, CASB, SWG, VPN, SIEM, and more. Point solutions try to give IT a better handle on the risk associated with the web.
But none of them focus on what's exposing the user to this risk - the browser.
Silo makes the browser a fully managed asset, improving security and governance while lowering costs.