Threat Intelligence Without Heavy Investment
Access and analyze suspicious or malicious content without exposing your resources or your identity. Silo for Research is a cloud-based, virtual browser platform for targeting, accessing and collecting data to support threat intelligence activity.
Request a Demo
Blend in - but don’t get caught!
Cybercriminals are paranoid, and if one aspect of the collection process seems suspicious, access to threat or fraud evidence will be quickly blocked. Cyber threat intelligence production demands an anonymous environment that enables researchers to blend into the environment without revealing intent or identity.
"230,000 new malware samples are produced every day — and this is predicted to only keep growing"
- Panda Security
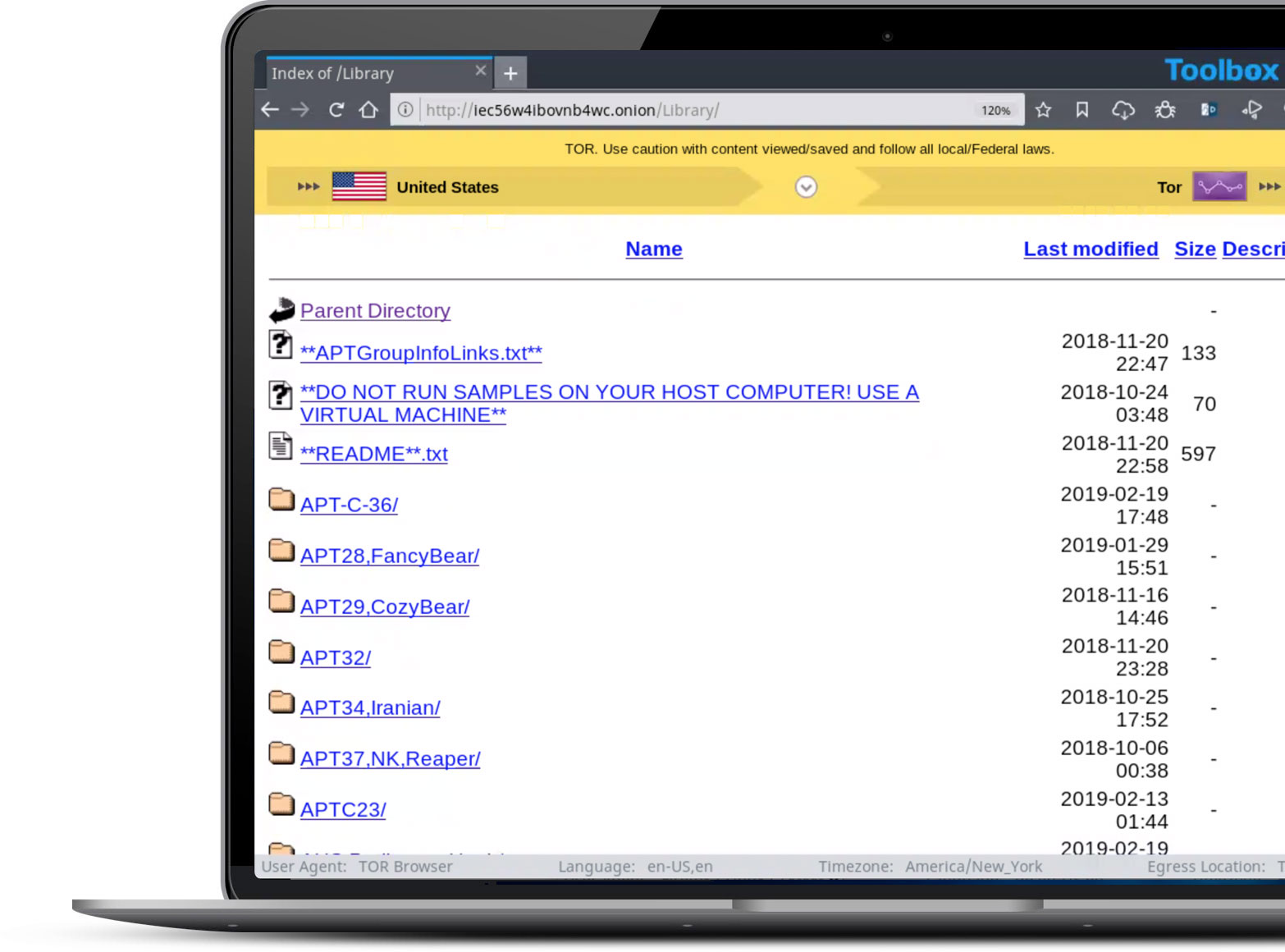
Rubber gloves for grabbing toxic code
Silo for Research is a managed attribution platform built in the cloud designed for the demands of cyber threat intelligence teams. Silo for Research provides a cloud-based virtual browsing platform that isolates the analyst from any web-borne threats, with attribution management tools to help researchers blend into the background.
Decrease the time to intelligence while improving analyst efficiency
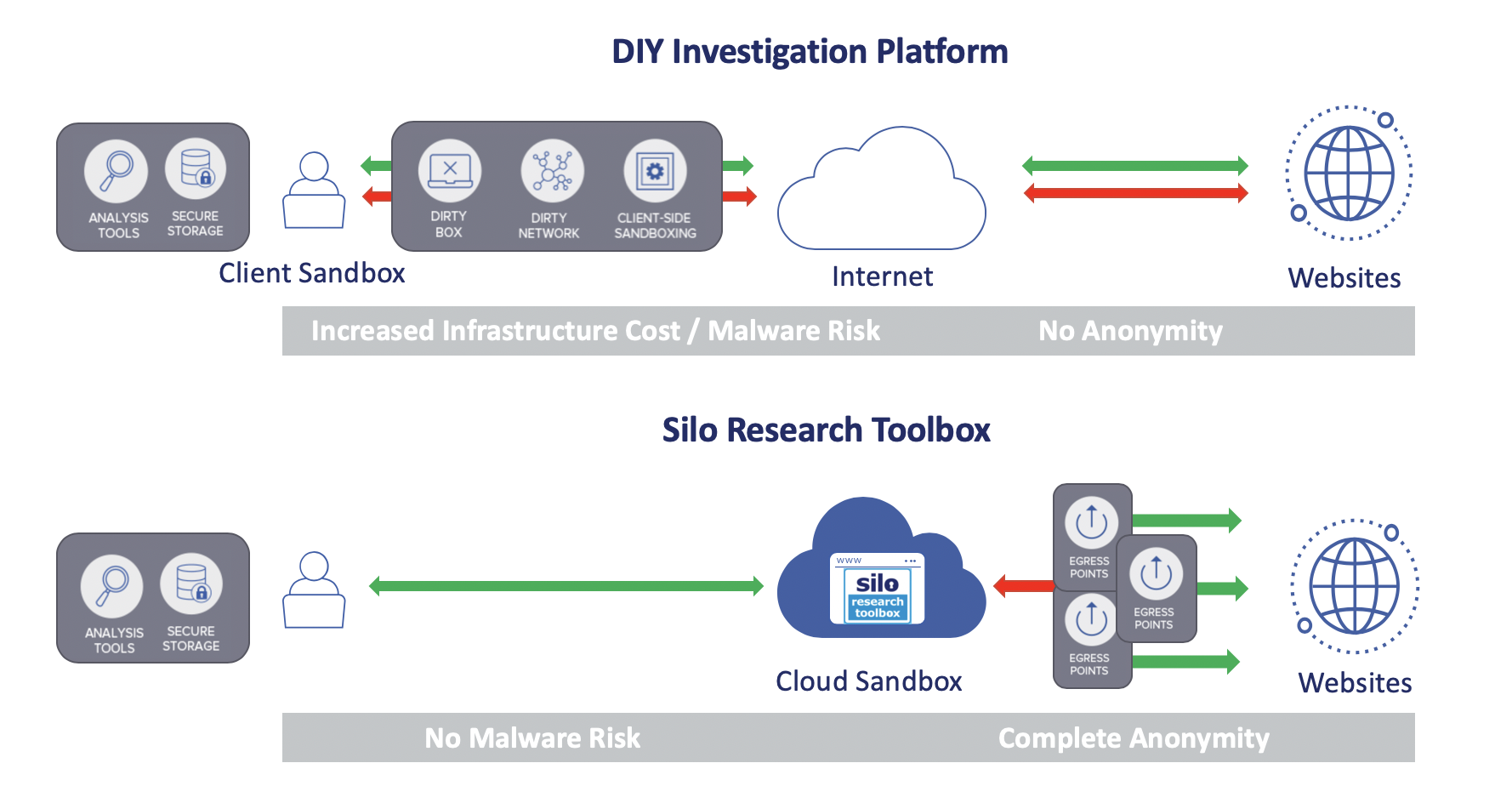
No more dirty lines, VPNs, and client-side sandboxing. Stop transiting malicious code across the corporate network and storing it on local resources. Silo for Research is an integrated, launch and go platform that gives full access to web based resources, deep analysis, and content capture, at arm’s length. Never touch toxic content and never expose your identity.
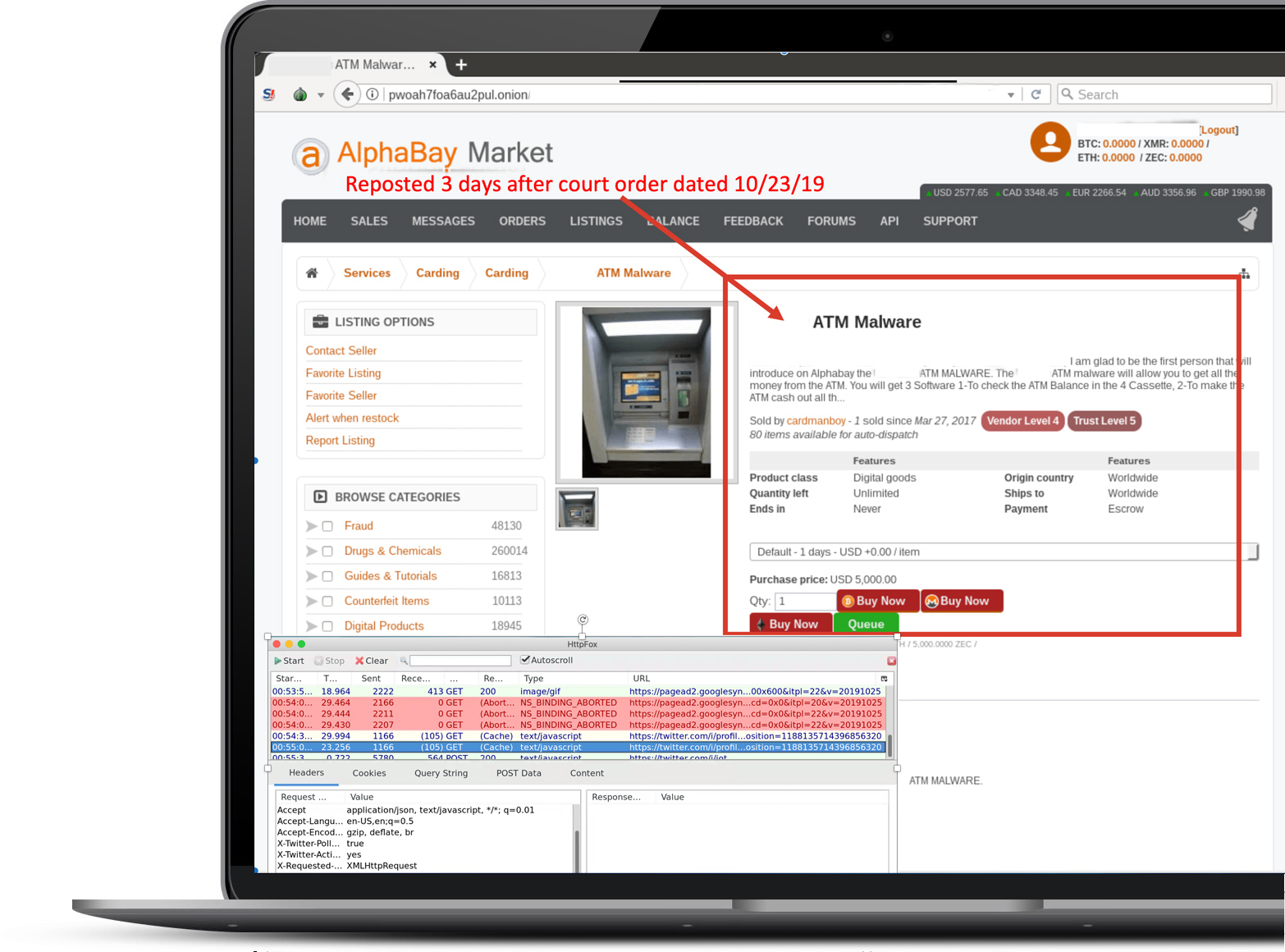
Analyze and capture in a single platform
With an unaltered view of web content - analysts can view source, trace cookie linkages, capture packets, and even binary code without tainting local resources. Content, either flattened or in its native form, can be stored in an encrypted cloud storage bucket and shared across research teams. Any web content accumulated in the remote cloud-browser session is purged at session close. Researchers get a fresh environment on the next session.
-
100% isolation of all web content off-device and off-network, isolating endpoints from malicious code, cookies, and trackers
-
Non-attribution of the analyst, or spoofed attribution through geographically distributed egress nodes
-
Disposable browser sessions, purging all cookies, trackers or other web content designed to surveil users
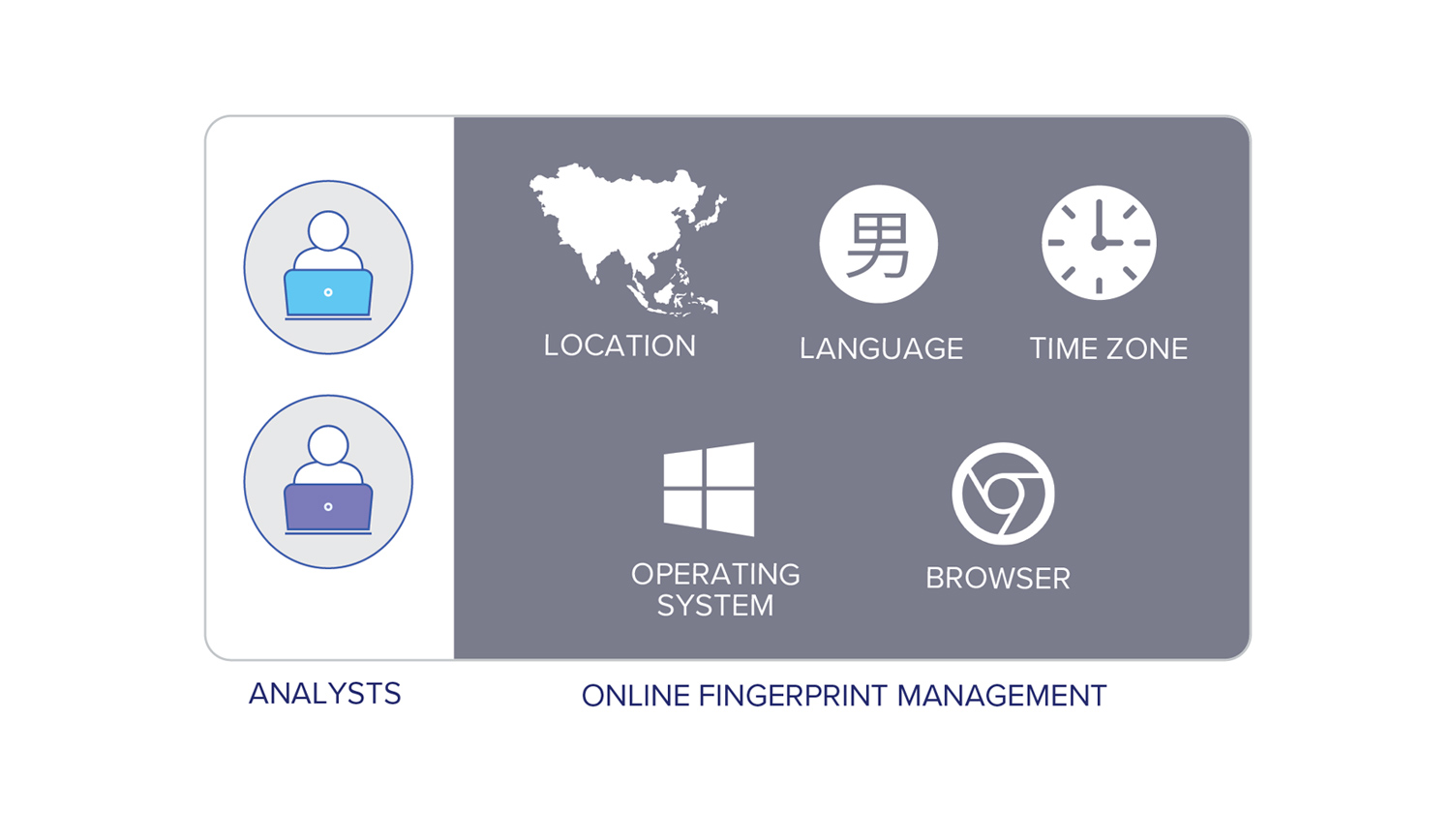
Obfuscate research activity with complete anonymity and localization
Tipping off the target of an investigation can ruin months for work. Silo allows customization of browser and platform parameters, including language, time zone, keyboard settings, and more. Analysts blend in to the local environment through a network of globally distributed egress locations.
-
Exit to the internet in the target region, even the dark web without revealing analyst IP information
-
Configure platform parameters specific to the environment
-
Translate foreign content after the fact, minimizing your footprint on the destination site
Collect evidence across multiple target properties and browsing sessions
Multiple, separate virtual instances support simultaneous collection actions across resources and networks. Share research materials with other investigators with cloud-based storage
-
Page content full fidelity and capture with annotation and integrated, encrypted cloud-based storage
-
Out-of-band language translation to convert to the local language without disclosing analyst intent
-
Analysis of web source content and IP packet transactions for deeper investigation into counter-party resources
Enforce analyst usage and compliance requirements while conducting research
Analysts need to access web resources that fall outside of standard corporate policies. Silo for Research logs all analyst activity in encrypted audit logs. Compliance teams can review analyst activity and remediate issues. Customer-managed encryption keys maintain a proper chain of control for non-repudiation of activity logs.
-
Centralized, comprehensive real-time logs of all user and admin web activity
-
Log data encrypted with customer-managed keys, with authenticated API-based extract
-
Download content timestamp and hash values logged to defend the authenticity of collections


